Are you currently using a virtual private network, or thinking to use it shortly; you probably want to know how it works? As a matter of fact, it seems like an intricate process involving the terms like tunneling and encapsulation.
As we all know that the virtual private network helps in securing the traffic you send or receive over your internet connection, so spies and hackers can’t see the IP (internet protocol) address or transmitted data. But, how it actually works?
Let’s get started with some of the important features of VPN.
VPNs — Private Networks Within The Internet
As the name suggested, VPN is a private network that can be accessible through several services such as Express VPN. When it comes to the data transmission (whether you can send it or receive it) on a VPN is split off from the entire internet including other PCs.
It is somewhat similar to the home/business network, which can be used to distribute files amid devices across the router. If you have the network, which is appropriately secured, no one outside the network can see the information transmitted; for instance by using WPA2 encryption. It is how the virtual private network provides you protection and security.
Also check : Setup a Second Wireless Router on your Home Network
VPN’s ‘virtual’ part makes the difference. The VPN will physically separate your home/business network from the rest of the internet and make it more secure. You can also share the limited files on it if you’ve unplugged the internet connection. In contrast, a VPN is accessed via the web.
Thus, your identity and data have to be protected in a proper manner.
Tunneled connections
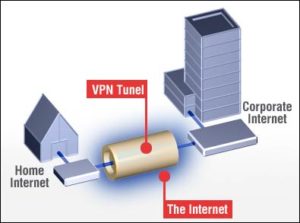
When it comes to the Tunneling, it’s the process by which you can privately send data over the Internet, through the VPN.
If you want to know how tunneling works; then keep on reading!
At the outset, you have to understand that the all the information/data transmitted through the internet is walled off into little pieces known as ‘packets.’ Each packet consist of information along with the protocol like BitTorrent, HTTP, Telnet and more), which is being used for and the sender and the receiver’s IP address.
When you say virtual private network’s tunneled connection, each data packet is positioned within the other data packet before sending through the internet. This procedure is known as encapsulation.
Now you can easily interpret that how useful the tunneling and encapsulation is when it comes to securing data. The outermost packet provides the stratum of security, which prevents the information to be viewed by the public.
Encryption
Now move towards encrypting the packets over the VPN. It’s not sufficient to just tunnel the transmitted information. The second step is to encrypt the data, where it is programmed so that the data can merely read by your virtual private network server or client that are linked together securely.
The VPN uses a lot of security protocols for data encryption. One of them is Internet Protocol Security (IPSec). It works in the following way;
- There’s a key for encryption, which will encrypt each encapsulated data packet and it is only shared between the virtual private network’s client and server.
- The process uses a sub-protocol a.k.a. Encapsulation header, which is helpful in hiding certain information during the transmission such as the identity of the sender.
VPN mentioned above features, and some others, such as VPN for torrenting, keeps your identity and data secure over the internet.
In short, three basic features make VPN (virtual private network) security work are tunneling, encryption, and authentic connections.
I hope, the information mentioned above regarding VPNs will apparently get you understand how it works and how they’re beneficial in today’s erratic internet world.





Comment here