Nowadays Cyber threat is a major problem in day to day life of technology where attackers always keep on digging to find the loophole.
One of the major and terrifying cyber threat is DoS and DDoS as its name implies it makes it prevents legitimate users from accessing information or services finally renders to unavailable.
What are DoS and DDoS Attack
Denial of service (DoS) : It uses a single Internet connection where an individual flood a target with fake requests usually in an attempt to exhaust server resources and continuously to keep the server from answering other legitimate requests.
Distributed Denial of Service Attack (DDoS) : As name indicates it is distributed here the group of attackers or any army also known as Botnets launch attack. The victim is flooded with huge fake traffic to take down servers for a very long time.
Nowadays DDOS is most frequently seen attack tend to target the network infrastructure. Most Multinational companies have been the victim of this nightmare ever after strengthening the security.
To make it more clearly let’s take an example of the real-time scenario.
You are getting continuously call from telemarketing or any third party department preventing you from receiving the call from your friend .Here telemarketing continues flooding your Mobile network with a large number of calls simultaneously.
Here Telemarketing service is Attackers who is performing DDoS or DoS
Different Layers of DDoS or Dos
- Layer 4 DDoS: Thousands of attackers or botnets bring down one server
- Layer 7 DoS: One attacker brings down one server
Layer 4 DDoS : The Most common attacks in the world of cyber threat and it considered as one of the higher profile threat to the companies.
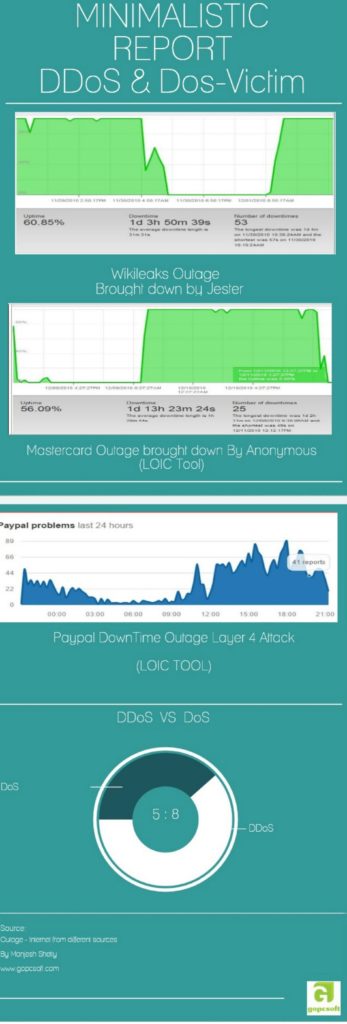
DDoS was known from ages , It is not a zero-day attack but 4chan’s Anonymous Hacktivist group made it hype in the world of CyberThreat.
Anonymous first target was Scientology websites in 2008 with the help of tool called LOIC + Botnets
Later Anonymous performed many DDoS attack on many major companies
- Amazon
- MasterCard
- Paypal and list go on.
Different Attack vectors in this category
- UDP flood
- SYN flood
- DNS amplification attacks
- Ping of death and more.
Their tool was Low orbit Ion cannon which is connect to IRC Server to command and control Botnet army.
Even Many other Hactivist group like LulzSec Attacks on Government Sites which includes FBI,CIA ,SOCA ,Sony and even US senate.
Attacker target is not us ,Their Main target is to bring down gaming server for example sony and other government websites.
Layer 7
we all know jester infamous black hat hacker who claims to be bring down Wikileaks website single-handed for more than a day.
According to Experts, he uses Slowloris tool with some variation to bring down websites without the help of botnets.
Different Attack vectors in this category
- HTTP flood
- DNS query Flood
- Slowloris attacks
Wrap up : Some people use Link-Local DoS: IPv6 Router Advertisement Attack where the attacker can bring down the whole network single handily .Even there are many Zero-day DDoS attacks which are used by many black hat hackers to take down websites.
All these points are written by me after watching DEF CON 🙂
Manjesh shetty is the Founder of GOPCSOFT & Co-Founder of SOSC Non Profit organization. He was Regioanl Coordinator of Mozilla during his college dats. He is a Part-time Tech Blogger, Mozillian, a Developer by passion, an open source contributor and FOSS enthusiast. His writing and Tech-talks focus revolved around Hacking, Techie Tutorials, SEO, and computer security.






Comment here