Art of Anonymous browsing online
Surfing anonymously isn’t as hard or as intimidating as it looks. But remember one thing practically there is no tutorial out there that will make you completely anonymous browsing. Being completely anonymous browsing is next to impossible.
Also check : Anonymous hackers from worldwide – Everything you need to know about them
For anonymous browsing, you have to go through all these Steps
- The Web Browser Security
- Masking IP Address
- Local Network Security
- Encryption/Logs
- Anonymous Based Operating System
Configure Web Browser security to Browse Anonymously

- Tor Browser
Tor is free software for enabling anonymous communication.Tor does not protect all of your computer’s Internet traffic when you run it. Tor only protects your applications that are properly configured to send their Internet traffic through Tor.To avoid problems with Tor configuration, For anonymous browsing online I recommend you use the Tor Browser. It is pre-configured to protect your privacy and anonymity on the web as long as you’re browsing with the Tor Browser itself.
Note: Just by installing Tor or Tor browser doesnt make you anonymous.
- Cookies
For anonymous browsing online,Cookies is also is the main factor that is a simple text file that is stored on your computer or mobile device by a website’s server and only that server will be able to retrieve or read the contents of that cookie. Each cookie is unique to your web browser. It will contain some anonymous information such as a unique identifier and the site name and some digits and numbers.In Simple words, Cookies are used to track your web activities. Here are the steps to get rid of cookies
There are plenty of Add-ons that you can use
Set your browser to not accept cookies from sites (Disabling cookies you won’t be able to access certain sites) or , at least, make sure that you remove cookies after browsing . I hope Everyone knows how to clear the cookies.
There are some cookies long-term cookies. Also Known as Local shared objects (LSOs), commonly called Flash cookies (due to their similarities with HTTP cookies), are pieces of data that websites which use Adobe Flash may store on a user’s computer.To remove this type of cookies there are several <ADD-ONS> or use can use <Flash Cookie Cleaner>.
Note : just because you are using Tor Browser you are safe from cookies
- HTTP referer :
It is an HTTP header field that identifies the address of the web page (i.e. the URI or IRI) that linked to the resource being requested. By checking the referrer, the new web page can see where the request originated.This can be used to track your path from page to page. Here is the simple Fix
In Firefox use can use ADD-Ons like Referer Control or you can do it manually .
In Firefox go to > about:config ,search for > network.http.sendRefererHeader. Once you’ve found it just set it to a value of 0.
In chrome, you can use <Referer Control>.
Note: These steps dont apply for internet explorer
- User Agent :
Today, nearly everyone uses a web browser as their user agent. You can anonymize your browser user agent by installing the addon to change/create custom User Agents.
Note: Partially anonymizing your user agent actually makes your header more unique, not less.
- Search Engine : Every time you use a regular search engine, your search data is recorded. Major search engines capture your IP address and use tracking cookies to make a record of your search terms, the time of your visit, and the links you choose – then they store that information in a giant database.check out Startpage. It sends your searches to their own server before actually sending it out to the web to help hide who’s searching.StartPage Protects Your Privacy!
Masking IP address and using Proxy to Browse Anonymously
When you connect to the Internet, your Internet Service Provider (ISP) assigns you an IP address. When you surf the web, view email or download a photo from the Internet, your activity can be tracked with your IP address. The IP address can be used to locate a person, and trace the Internet activity.anonymous browsing online and protect your privacy, you’ll need to hide your real IP address.

- Proxies :
Mask your IP address with Proxies . Another thing to look at is the different kinds of protocols a proxy may use. The main kinds of proxies you will here about are SOCKS proxies and HTTP proxies.SOCKS proxies are lower-level than HTTP proxies. SOCKS uses a network handshake to send information about a connection. The SOCKS proxy then opens a connection, perhaps through a firewall. HTTP Proxies are transported over TCP and forwards an HTTP request through and HTTP server. One simple way to look at it is that HTTP proxies are web-based(obviously), and SOCKS proxies are machine based.There are thousands of free web proxy servers that you can use to hide your IP address and surf anonymously. Browsing through a proxy means that you are not accessing a website directly, but going through an intermediate “proxy” which relays the information back and forth between you and the destination website. list of Proxy sites
Also check : bypass video streaming sites like putlocker
- VPN:
Virtual Private Network (VPN) offers a connectivity to another network, and when connected your computer receives a new IP address from a VPN provider. Every traffic from your computer routes through the VPN network, so your true IP address assigned by your ISP is hidden. Aside from hiding your IP address, using VPN allows you to access any network even though your network may be geo-restricted. They help you get on the Internet with a different IP address than the one provided by your ISP.
There’s a major difference between proxies and VPNs.
proxy == anonymous(more or less)
VPN == private(Virtual PRIVATE Network)
Editor Choice : HideMyAss VPN
download HideMyAss VPN for Free and get upto 43% OFF on 12 Months Plan
<cyber ghost is also one of the best VPN software >
Note: don’t use openVPN for anything illegal Activities. Never buy a VPN from your personal credit card or from your real name
- Proxy Chaining:
It’s a very useful tool and it’s easy to use. With this tool, you can chain proxy to proxy, proxy to VPN, proxy to VPN to Tor(if you want), proxy to proxy to proxy to proxy to proxy to VPN to the proxy.It’s like a chain every time it changes
It is More Secure: Instead of connecting to the internet through just one proxy you will be able to access the internet through several proxies and, as a result, will enjoy better security.
It is More Reliable: Since you’re using more than one proxy it will be difficult to guess your IP and as a result difficult to hack into your network. Of course, this particular technique has its own vulnerabilities but it is more reliable than using just one proxy.
It is Less Stressful: You don’t have to worry about changing your proxy every hour. A good proxy chain can last longer before you start experiencing problems.
Tweak Local Network Security to Browse Anonymously
 MAC Address:
MAC Address:
Your MAC address is a 48bit hardware identifying address which is part of your network card. Everyone has one and they are all unique. media access control address (MAC address), also called physical address, is a unique identifier assigned to network interfaces for communications on the physical network segment. MAC address is “burned into” a given device from the factory. A MAC address takes the form of six pairs of hexadecimal digits.MAC addresses allow communication between devices on a local network.
how to find MAC address in windows open CMD > type config /all
How to spoof/change your MAC address:
For Windows: <Technitium MAC Address Changer>
Also check : how to bypass blocked torrent
Note: change your IP address doesnt make you anonymous on the internet, you can be tracked down with MAC address which is still there, not spoofed
- DHCP:
Dynamic Host Configuration Protocol (DHCP) is a client/server protocol that automatically provides an Internet Protocol (IP) host with its IP address and other related configuration information such as the subnet mask and default gateway.You DHCP client will often transmit some information when requesting an IP address. Much of the time this only includes your hostname and MAC address.it transmits a hell of a lot more. It will transmit your hostname, DHCP cd version, kernel, OS, and architecture. This is known as your vendor class id. Which is obviously very identifying. This can be taken care of by editing your /etc/dhcpcd.conf file.
instead of having your actual hostname and vendor class id be transmitted you can change it to whatever you want using <Wireshark>
Note: Not to have a unique or identifying user and hostname.
Encryption/Logs

- Stacked Encryption:
This is a when an encrypted filesystem is stacked on top of an existing filesystem. This causes all files written to the encrypted folder to be done so “on the fly” before being written to disk.
– eCryptfs
– EncFS
- Block Device Encryption:
This, on the contrary, is written below the filesystem layer to make sure that everything written to a certain block device is encrypted.
– dm-crypt + LUKS
– Truecrypt
- Logs :
Logs can let someone know what you have been doing on your system. Be aware of hiding logs files and don’t break your head too munch . You can google for more information about logs
Note: dont mess with som files Destroying certain files could do serious damage to your OS it would be nightmare
Anonymous Based Operating System : To Browse Anonymously on the Internet
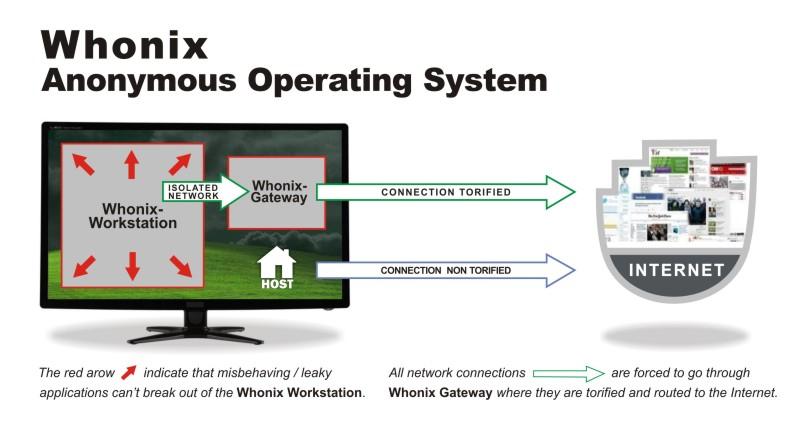
Good idea is to install some anonymity based OS like <Whonix> .Whonix is an operating system focused on anonymity, privacy, and security. It’s based on the Tor anonymity network[1], Debian GNU/Linux[2] and security by isolation.
Even you can create Live USB for one-time use which increases chances of anonymity.
MISC :
Software Like weather monitoring could be very bad because they may transmit zip codes or address information to get local weather reports. Many people overlook this. Hiding your IP won’t matter if you overlook this.
Also check: Top 5 network hacking tool
This tutorial doesn’t make you 100% Anonymous.Remember we cant Browse Anonymously completely FBI or CBI can find you within a blink of eye ,so don’t try any Trying illegal Activities.
Thanks to Lucid(evil one) I was able to collect all these Points
This tutorial for educational purposes only
Manjesh shetty is the Founder of GOPCSOFT & Co-Founder of SOSC Non Profit organization. He was Regioanl Coordinator of Mozilla during his college dats. He is a Part-time Tech Blogger, Mozillian, a Developer by passion, an open source contributor and FOSS enthusiast. His writing and Tech-talks focus revolved around Hacking, Techie Tutorials, SEO, and computer security.





Comment here